
Raffensperger’s Stunning Refusal to Correct Serious Breaches in Georgia Voting Machines
By M Dowling
According to County Local News, Georgia Secretary of State Brad Raffensperger refused to testify under oath about the reliability of Dominion Voting Machines. This is a very big deal since the machines were found to have serious potential breaches.
According to a tweet by Leading Report, Raffensperger has not only refused to testify under oath but has also delayed the installation of Dominion’s security patches until after the 2024 presidential election.
Professor Halderman, who researched the machines’ reliability, also tweeted out that Georgia Secretary of State Brad Raffensperger will not install Dominion’s security patches before the 2024 election.
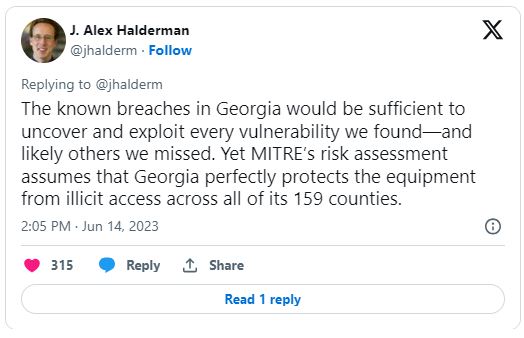
“The known breaches in Georgia would be sufficient to uncover and exploit every vulnerability we found—and likely others we missed. Yet MITRE’s risk assessment assumes that Georgia perfectly protects the equipment from illicit access across all of its 159 counties.
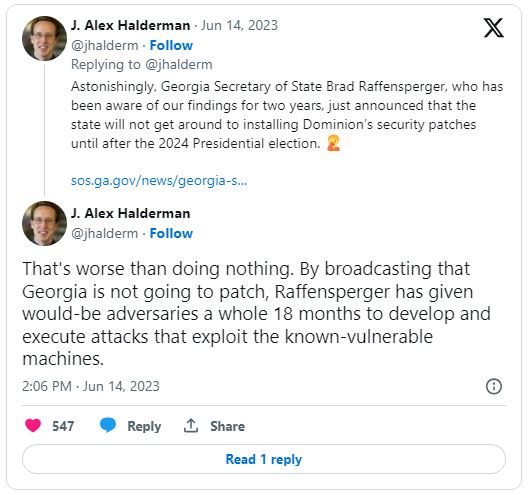
“Astonishingly, Georgia Secretary of State Brad Raffensperger, who has been aware of our findings for two years, just announced that the state will not get around to installing Dominion’s security patches until after the 2024 Presidential election.”
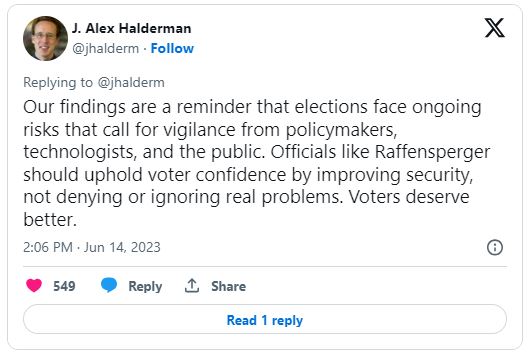
Professor Halderman conducted the highly-respected study exposing the flaws in the Voting Machines and is stunned by the failure of Secretary of State Raffensperger’s refusal to correct the problems.
NO REASON GIVEN
Raffensperger has not provided a specific reason for his refusal to testify. As the Secretary of State, Raffensperger plays a crucial role in overseeing the state’s elections and ensuring their fairness and accuracy.
Furthermore, the delay in installing Dominion’s security patches has raised concerns about the vulnerability of Georgia’s election system. By postponing the installation of these patches until after the 2024 presidential election, Raffensperger is leaving the system exposed to potential risks and attacks.
The timing of Raffensperger’s decision is also significant. With the 2024 presidential election approaching.
Raffensperger has defended his actions, stating that the delay in installing security patches is due to the need for thorough testing and evaluation. He claims that rushing the installation process could potentially lead to more problems and vulnerabilities.
He knew about this for two years like the rest of us.
According to County Local News, he won’t even install the pilot program machines with the patches. By the way, he is a Trump hater.
THE HALDERMAN REPORT
Far-left Georgia Judge Amy Totenberg sealed and covered up the results of the investigation on Dominion voting machines in Georgia and sat on the report for two years until its release last summer.
The nonpartisan study by Professor Haldeman is highly respected and widely accepted on all sides of the aisle.
According to a sworn declaration, security expert J. Alex Halderman identified “multiple severe security flaws” in Georgia’s touchscreen voting machines that should be addressed to protect the integrity of elections.
Halderman told AP that he saw no evidence that the flaws were exploited during the 2020 election, yet “there remain serious risks that policymakers and the public need to be aware of” and must be fixed for future elections.
Dr. Halderman identifies seven major vulnerabilities:
- Attackers can alter the QR codes on printed ballots to modify voters’ selections
- Anyone with brief physical access to the BMD machines can install malware onto the machines
- Attackers can forge or manipulate the smart cards that a BMD uses to authenticate technicians, poll workers, and voters, which could then be used by anyone with physical access to the machines to install malware onto the BMDs (id.);
- Attackers can execute arbitrary code with supervisory privileges and then exploit it to spread malware to all BMDs across a county or state (id.);
- Bad actors can alter the BMD’s audit logs (id.);
- Attackers with brief access to a single BMD or a single Poll Worker Card and PIN can obtain the county-wide cryptographic keys, which are used for authentication and to protect election results on scanner memory cards (id.); and
- A dishonest election worker with just brief access to the ICP scanner’s memory card could determine how individual voters voted (id.).
He noted that bad actors, both foreign and domestic, could recruit election workers to corrupt the election.